Out of curiosity, can you validate if these bytes are correct for the FileKey and the HeaderData XOR on the boot.bin you provided (this is printed from inside meDecryptDiskContentKey())? Just trying to pinpoint where exactly this is going wrong...You should only run bootstrap once, to have it create a makefile that is correct for your platform. I once tried to edit the makefile by hand to insert ifdefs and I ended with a file that failed at cryptography, just like yours. I suggest you start over from the original source tree, only run bootstrap once then use make/clean to recompile after modifying. You can keep the current files on a different place and move over the mods once it builds a exe that works properly. I suggest you first try to build a file that works properly with PS2 memory cards.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Thread starter doccaz
- Start date
l_oliveira
Professional
Out of curiosity, can you validate if these bytes are correct for the FileKey and the HeaderData XOR on the boot.bin you provided (this is printed from inside meDecryptDiskContentKey())? Just trying to pinpoint where exactly this is going wrong...
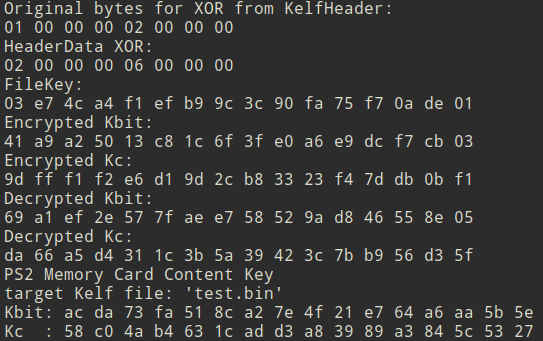
I'd like to call your attention to this:
ARCADE_KBIT=69A1EF2E577FAEE758529AD846558E05
ARCADE_KC=DA66A5D4311C3B5A39423C7BB956D35F
From: https://www.psdevwiki.com/ps2/Talk:Keys#Etc_keys
Which mean the content keys decrypted successfully and the rest of the file should decrypt properly as well.
I think there is a version of kelf-tool which has been compiled with COH keys, that can decrypt these files with the correct DISC encrypted keys.
l_oliveira
Professional
Get pre compiled or build kelf-tool.exe and then put this file named "PS2KEYS.dat" at the root directory of your user profile. Then you can use it to decrypt the boot.bin file I posted. This file has correct keys to decrypt coh boot.bin but it will only work if it is of the disc type.
Edit: To convert any file to disc type just paste this 32 bytes at offset 0x28 of the boot.bin file:
41A9A25013C81C6F3FE0A6E9DCF7CB039DFFF1F2E6D19D2CB83323F47DDB0BF1
Notice that this will only work for the boot.bin files from COH cards.
Edit: To convert any file to disc type just paste this 32 bytes at offset 0x28 of the boot.bin file:
41A9A25013C81C6F3FE0A6E9DCF7CB039DFFF1F2E6D19D2CB83323F47DDB0BF1
Notice that this will only work for the boot.bin files from COH cards.
Attachments
Last edited:
Don't forget to run dos2unix on the attachment if building kelftool for *nix...Get pre compiled or build kelf-tool.exe and then put this file named "PS2KEYS.dat" at the root directory of your user profile. Then you can use it to decrypt the boot.bin file I posted. This file has correct keys to decrypt coh boot.bin but it will only work if it is of the disc type.
Edit: To convert any file to disc type just paste this 32 bytes at offset 0x28 of the boot.bin file:
41A9A25013C81C6F3FE0A6E9DCF7CB039DFFF1F2E6D19D2CB83323F47DDB0BF1
Notice that this will only work for the boot.bin files from COH cards.
BilonFullHDemon
Student
What can I do after the file is decrypted?Get pre compiled or build kelf-tool.exe and then put this file named "PS2KEYS.dat" at the root directory of your user profile. Then you can use it to decrypt the boot.bin file I posted. This file has correct keys to decrypt coh boot.bin but it will only work if it is of the disc type.
Edit: To convert any file to disc type just paste this 32 bytes at offset 0x28 of the boot.bin file:
41A9A25013C81C6F3FE0A6E9DCF7CB039DFFF1F2E6D19D2CB83323F47DDB0BF1
Notice that this will only work for the boot.bin files from COH cards.
l_oliveira
Professional
What can I do after the file is decrypted?
I don't know, maybe decompress it then analyze it on IDA or other disassembler (yes it is compressed, with a self decompress asm stub).
they are called wedges, i think prolific quit producing them. i will look when i get back to the lab@extraweb1 what kind of probes are these ?
the wedges a really expensive $600 USD worth. (edit) they are "agilent wedge probe"
my plan is to make asics so we don't have to sacrifice dongles
Last edited:
Once I do figure out why this thing don't work properly when compiled I wanna make the encryption keys external like kelftool (maybe use the same format and paths also). So that I have a better tool to work with during my research into the asic.
It's crazy this all started with a accident

 , but this has been fun so far.
, but this has been fun so far.
It's crazy this all started with a accident
lunasea0083
Beginner
Goodjob, now sign a boot file (I don't mean copy the bytes with a hex editor
I have original asic cxd9600R,cxd9600ar,& cxd3740 that were originally used in the cards I'm just trying to get a better understanding of the asic so I can program some. I had a decapping done and code exploration is being done now and hopefully programming original asic will pay off.
Last edited:
l_oliveira
Professional
Seriously you don't need to make ASICs, and those are likely SoCs, a tiny mcu with security enclave and a firmware. We have the keys, it should be simple make a dongle out of a raspberry pico.
Would love to, these dongle's were used in more things (devices)than most know. Also the Sony chip is not a simple Soc I have layer views from decapping. It is close in tech to cipherchain chip like addonics. it is a security asic, but these days everything is considered a SOCSeriously you don't need to make ASICs, and those are likely SoCs, a tiny mcu with security enclave and a firmware. We have the keys, it should be simple make a dongle out of a raspberry pico.
Last edited:
Mitchbrain
Beginner
I've also been trying to get binding to work, I got the tool compiled (I used libusb-compat-0.1-0.1.8, MSYS on windows), I can dump cards but I can't get them to boot properly. Binding boot after 'decrypting' it using the the magic hex key at offset 0x28 doesn't result in the same key after re-binding it. I'm really starting to wonder if the version of ps3mca that can be found is complete. Can someone verify that they got this to work using the zip labeled jimmikaelkael-ps3mca-tool-12a198f, it has sha1 hash of B5315A5530D051E130D83D966CFD2E06F207170B.
I have been over the code a few times and i honestly cant remember what is supposed to change.I've also been trying to get binding to work, I got the tool compiled (I used libusb-compat-0.1-0.1.8, MSYS on windows), I can dump cards but I can't get them to boot properly. Binding boot after 'decrypting' it using the the magic hex key at offset 0x28 doesn't result in the same key after re-binding it. I'm really starting to wonder if the version of ps3mca that can be found is complete. Can someone verify that they got this to work using the zip labeled jimmikaelkael-ps3mca-tool-12a198f, it has sha1 hash of B5315A5530D051E130D83D966CFD2E06F207170B.
I thought it was discussed long ago that part 2 of the decrypt function needs changed but i lost so many things the only one who could tell you won't.