El_isra
Enthusiast
Hello everyone. as some of you may know. I've began analyzing the SoulCalibur 2 conquest cards with the intention of replicating them as well as fixing damaged ones (and maybe other things in the future)
For investigation purposes. I need as much dumps as possible. so if you own both a conquest card and a PS3 mc adapter (Sorry! current lack of information at the moment keeps me scared enough to not even try making a dumper that works from a console. so for now, let's keep it at ps3 adapter dumps)
Another detail, I'm not only after the dump, but also from some data of the card...
The data I'm after is:
NOTE1: if the dump is too slow (2 pages per second) please cancel the dump, unplug and replug the adapter and try again. as slow dumps seem to produce corrupted data
To obtain all the needed information, you will need to use My fork of ps3mca-tool
the config INI file must be set up to use retail magicgate, and also, remember to put the verbosity level at 5 so that all the important data is printed on screen
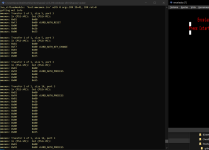
It should look something like this
For investigation purposes. I need as much dumps as possible. so if you own both a conquest card and a PS3 mc adapter (Sorry! current lack of information at the moment keeps me scared enough to not even try making a dumper that works from a console. so for now, let's keep it at ps3 adapter dumps)
Another detail, I'm not only after the dump, but also from some data of the card...
The data I'm after is:
- All the information provided by the -i command of ps3mca
- The conquest card security vectors (CardIV, CardNonce and CardSeed)
- The actual dump (with the -imgecc command)
- an MD5 hash of the dump just in case
- the number on the bottom right corner of the backside label (if possible)
NOTE1: if the dump is too slow (2 pages per second) please cancel the dump, unplug and replug the adapter and try again. as slow dumps seem to produce corrupted data
To obtain all the needed information, you will need to use My fork of ps3mca-tool
the config INI file must be set up to use retail magicgate, and also, remember to put the verbosity level at 5 so that all the important data is printed on screen
It should look something like this
Less:
Using 'retail' keys
CardIV: 01 11 A2 00 14 02 02 61
CardMaterial: 01 01 52 44 01 90 F5 71
context.UniqueKey: BD 5E 4F 72 52 88 5D FB 41 D2 40 A6 70 1C FE A3
CardNonce: 3C 83 8C A2 58 38 63 D9
MechaChallenge1: 5C 00 50 43 E2 08 58 A1
MechaChallenge2: D1 81 12 4C F9 A0 94 68
MechaChallenge3: 8A 9F F1 A4 42 9E 26 F8
CardResponse1: 04 1A 6D B7 5F D9 E2 34
CardResponse2: 7F 7B D4 0A 68 FC AC BC
CardResponse3: 58 42 5F CF 2A 1D C8 F5
context.SessionKey: 21 12 DD DA F9 E9 B7 2A
-- Conquest Card detected
System246 SoulCalibur2 Conquest Card Information
Page size : 512 bytes
Block size : 16 pages
MC size : 8 MB (16384 pages)
Card Flags : 0x2B:1|1|0|1|0|1|0|0|
-- MC claims to support ECC
-- MC claims to support bad blocks management
-- erase byte: 0xFF