I'm going to guess 0x100000 - since TS pointed out with the jumpers on the PAL it booted, but froze which would suggest it read the bootstrap ok then froze up when it got to the next step
@twistedsymphony - out of pure interest, what happens if you run the modified code with removing the ASIC and NOT installing jumpers on the PAL?
0x100000 is correct, and you need the ASIC present on board to 'unwrap' the code.
We already tried running unencrypted code, but i don't think this dump was tested.
(The three dumps i posted before still offloaded protection calculations to the ASIC.)
I.E. the unencrypted code i posted before wasn't patched like this one.
The rom i posted yesterday is the AMB version which has ASIC dependencies removed and is encrypted for the KBD asic.
When i get back home i can make an unencrypted version of this rom if it's needed as well.
I'll try to explain a bit of the ASIC functions for clearness, simplified

The DDP DOJ Asic on the real board has two functions. MAME does the following:
- It 'unpacks' the encrypted rom on startup (A)
- It can be used for calculations, but the ASIC contains some secret parts of the formula, and the answers must be correctly returned. (B)
A) The unpacking we can work around by loading data and having it packed by Mame and swapping the correct bytes say with UCON.
B) The calculating protections were patched in the AMB roms. (I don't have any dumps of other sources, so this is all based on his work as far as i can see.)
So for the rom i posted yesterday, this is the AMB version (no protection anymore) decrypted, and then re-encrypted for use with the killing blade ASIC.
If it is booted on a Killing Blade board, it should decrypt itself and work. For some reason we (at least i) don't get yet, it doesn't work.
That being said, it would be cool if someone shared dump(s) of other carts they got from China to get an idea what is really going on.
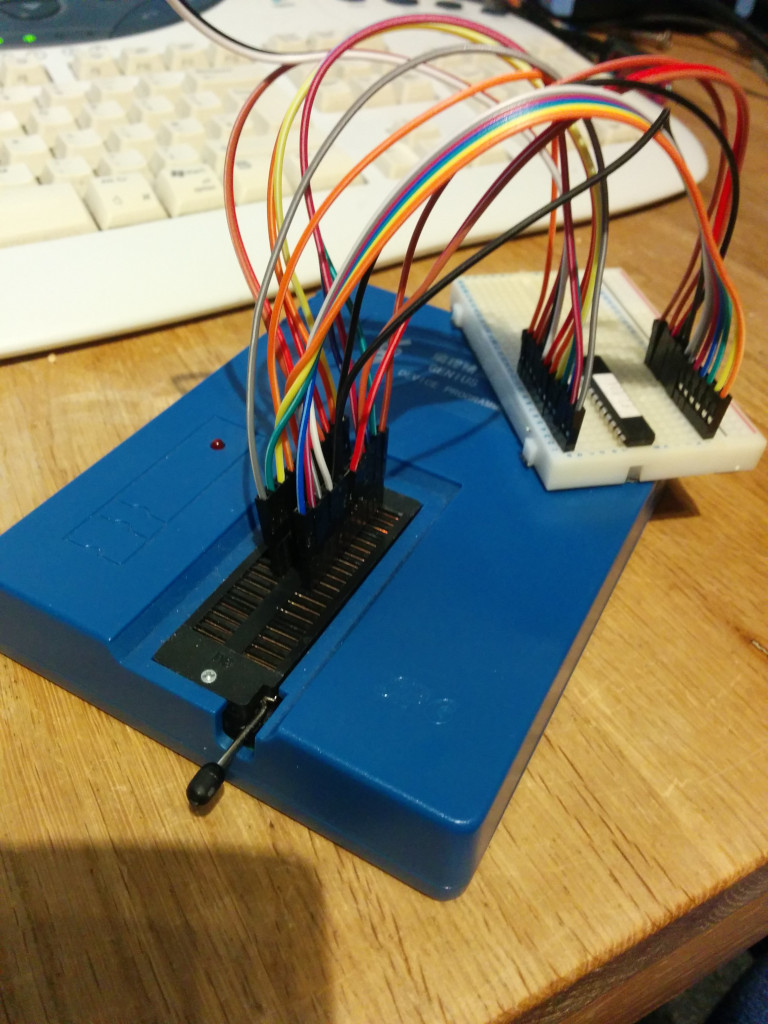

 This will probably not work for any possible 22V10 in the wild, but you can guess what are inputs and outputs based on the schematic.
This will probably not work for any possible 22V10 in the wild, but you can guess what are inputs and outputs based on the schematic. )
)